Aws Cloud Backup Things To Know Before You Get This
4 Easy Facts About Ec2 Backup Shown
Table of ContentsThe Definitive Guide to Rto10 Easy Facts About S3 Cloud Backup ExplainedThe Ultimate Guide To Protection Against RansomwareEverything about Aws Backup
energies that enable you to check and filter network traffic. You can utilize firewall programs to ensure that only licensed customers are enabled to accessibility or transfer data. controls that aid you validate credentials as well as ensure that customer benefits are applied properly. These procedures are commonly made use of as part of an identity and access management (IAM) service as well as in combination with role-based gain access to controls (RBAC).Encryption shields your information from unauthorized accessibility even if information is taken by making it unreadable. Endpoint protection software program normally enables you to check your network perimeter and also to filter web traffic as required.
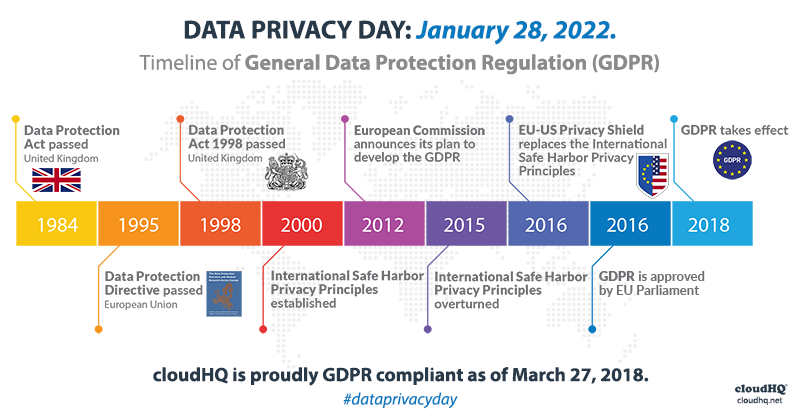
This can be done after information is processed as well as analyzed or regularly when data is no much longer pertinent. Erasing unneeded data is a need of numerous conformity laws, such as GDPR. For even more info about GDPR, look into our overview: GDPR Data Defense. a set of techniques as well as technologies that identify how an organization deals with a catastrophe, such as a cyber strike, all-natural catastrophe, or large-scale devices failure.

Not known Details About S3 Cloud Backup
Lessening your data collection can also assist you save on bandwidth and storage space. These systems make use of third-party information to verify users and also eliminate the demand to shop or transfer user information to your systems - https://www.industrybookmarks.com/author/clumi0/.
Showing this, GDPR has made customer approval a crucial aspect of information usage and collection. You can be sure to include customers as well as their consent in your procedures deliberately personal privacy worries into your user interfaces. s3 cloud backup. Having clear individual notices laying out when data is accumulated and why. You must likewise include options for customers to modify or opt-out of data collection.
Information portability is a crucial need for several modern-day IT companies. It means the capability to relocate information between different atmospheres and also software program applications. Extremely commonly, data transportability means the capability to relocate data in between on-premises information centers and the general public cloud, and also between different cloud carriers. Data mobility additionally has legal implicationswhen information is kept in various countries, it is subject to different regulations and also guidelines.
Things about Ec2 Backup

This makes it hard to relocate information from one cloud to one more, as well as develops vendor lock in. Progressively, organizations are trying to find standard means of keeping and also taking care of data, to make it portable throughout clouds. Smart phone protection refers to steps made to safeguard delicate info saved on laptops, smart devices, tablet computers, wearables and also various other portable tools.
In the modern-day IT atmosphere, this is a critical aspect of network security. There are several mobile data safety and security devices, designed to safeguard smart phones and data by recognizing hazards, creating backups, as well as stopping threats on the endpoint from reaching the business network. IT team usage mobile data protection software to make it possible for protected mobile accessibility to networks and systems.
Ransomware is a kind of malware that secures individual data and requires a ransom in order to launch it. New sorts of ransomware send out the information to opponents before encrypting it, enabling the opponents to extort the company, endangering to make its sensitive info public. Back-ups are an efficient defense against ransomwareif a company has a current copy of its data, it can recover it and also reclaim accessibility to the data.
Little Known Questions About Aws S3 Backup.
At this phase ransomware can contaminate any connected system, consisting of backups. aws s3 backup. When ransomware spreads to back-ups, it is "game over" for information protection strategies, due to the fact that it becomes impossible to click to find out more recover the encrypted data. There are several techniques for protecting against ransomware and particularly, avoiding it from infecting back-ups: The simplest method is to make use of the old 3-2-1 back-up policy, maintaining three duplicates of the information on 2 storage space media, among which is off facilities.
Storage space suppliers are using immutable storage space, which makes certain that data can not be changed after it is stored. Discover just how Cloudian protected storage can help protect your back-ups from ransomware. Big organizations have actually numerous datasets kept in various places, as well as much of them might replicate information between them. Duplicate information develops multiple problemsit increases storage expenses, develops variances and also functional problems, as well as can also cause safety and security and conformity difficulties.
It is no use protecting a dataset and also ensuring it is certified, when the information is duplicated in one more unknown location. CDM is a type of option that detects duplicate information and helps handle it, comparing comparable information as well as allowing managers to erase extra copies. Catastrophe recuperation as a solution (DRaa, S) is a handled service that gives a company a cloud-based remote catastrophe recuperation site.
With DRaa, S, any size company can replicate its neighborhood systems to the cloud, and quickly restore procedures in case of a calamity. DRaa, S solutions leverage public cloud framework, making it possible to keep several duplicates of framework and information across numerous geographical places, to boost resiliency. Data security needs effective storage innovation (https://www.postarticlenow.com/author/clumi0/).